Reverse
re1
附件:https://www.yk2er0.fun/2020/11/25/nctf2020/re1
1 | def encode(a1,a2): |
先ida看,字符串引用找到加密处
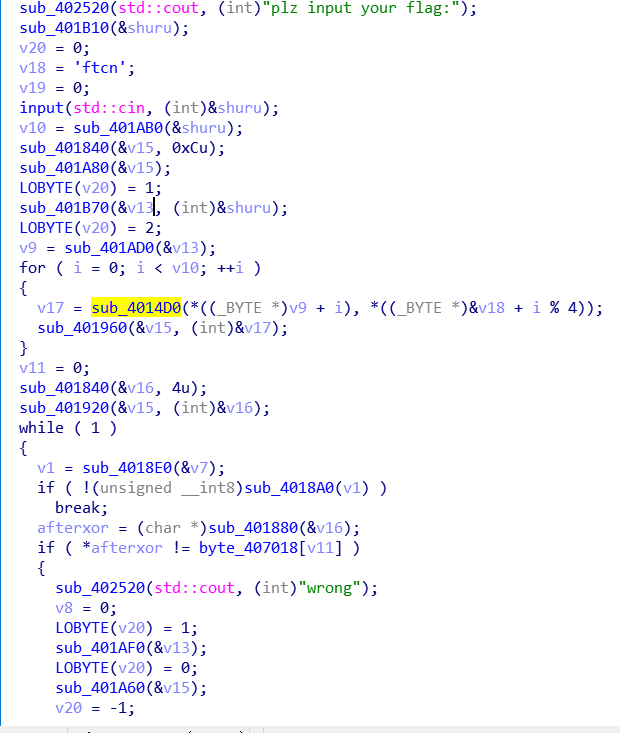
提取异或后的字节:
1 | a=[] |
win的字符串逆过来是倒着的.
开爆.
当时脑子抽抽了,忘记加密函数返回的是char类型,要多异或255.
re2
附件:https://www.yk2er0.fun/2020/11/25/nctf2020/re2
输入字符串长度为28
重写一下判断函数
1 | v4 = sub_1270((__int64)&unk_40E0); |
byte_40A8还有个自加密:
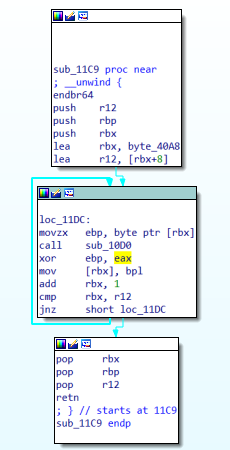
IDA下断动调之后可以看出是
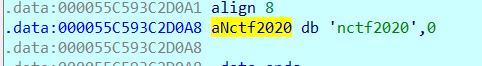
识别sub_1270为换表base64,写脚本:
1 | import base64 |
re3
通过字符串搜索找到sub_402090,
sub_401AE0()有
1 | ModuleName = [110, 26, 10, 2, 2, 64, 10, 2, 2, 0] |
解出ModuleName=tdll.dll
ProcName=tSetInformationThread
通过re3的程序框图,可以看出是先执行的sub_401060,其又调用了sub_401C50